May 7 2018
There are times when it is inconvenient or difficult to keep a key file secure -- I want to manage a disk using only a password. This is solved using "Ad Hoc" keys, temporary keys where the internal secret is derived strictly from the password. There is no key file and the secret is never written to disk.
Ad hoc keys are slightly less cryptgraphically secure than key files because there is less entropy in a password than the very large random secret in the key file. However, since the data is encrypted using the same very strong ciphers and the secret is generated using the same Argon2 hash the data will still be uncrackable if I use a complex password. The biggest difference is that the security of the data now rests entirely on keeping the password secret.
An ad hoc key needs to be recreated for every session, but using
the same password will always generate exactly the same key. The
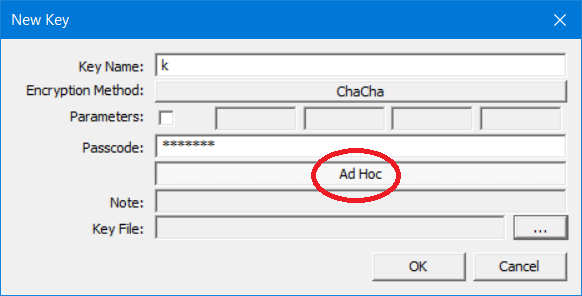
ad hoc key can be created using the "New Key" dialog.
Menu > Key > New...
Enter a name and password. I must provide a name so I can select
it later, but it can be a single letter since it this is a temporary
key. Click the "Ad Hoc" toggle. This will disable the "Notes" and "Key
File" boxes since the ad hoc key will never be saved to a file. Click
OK to create the key.
NOTE: If I change the encryption method or parameters, I will need to select the same method and parameters every time I recreate the key.

An ad hoc key can also be created from the command line:
KEY ADHOC <name> ["password"]
I can then create a new disk using the ad hoc key, or mount an existing disk by specifying the key name.
A good SecOps practice is to use a small ad hoc disk (a disk created with an ad hoc key) to store all your key files.
Comments are moderated. Anonymous comments are not visible to others until moderated. Comments are owned by the author but may be removed or reused (but not modified) by this site at any time without notice.